Project update 2 of 10
Price Cut, Product Inspiration, and What Makes This One Special
by Omar YoussefGreetings, everyone! We are proud to release our first update, with many more to come. Let’s start with some exciting news: in consultation with Crowd Supply, we have decided to reduce the price of Diabolic Drive from $111 to $99! We managed to do so by securing better quotes from new electronics resellers, which will also help us further mitigate component-availability risks. Because the majority of our components are now readily available locally, we also expect to begin assembly sooner than we had previously thought possible.
With that said, let’s dive into the update!
The Background, the Application, and the Challenge
Diabolic Drive was inspired by Episode Three of the YouTube series, "Hacking Google," in which Daniel Fabian, the leader of Google’s red team, was described as having the most "Diabolical" title in company. The word stuck with me and inspired the name for this product, which is my first red-teaming hardware tool.
A so-called "rubber ducky" looks like an innocent flash drive but behaves like a Human Interface Device (HID) capable of typing (or "injecting") predetermined characters as if it were a keyboard connected to the computer into which it has been inserted. These "keystrokes" can be utilized for various purposes, such as obtaining remote access to the target computer, copying data from it, disabling security features, or installing malware. These are all common objectives of "Red team" security audits, during which one or more "penetration testers" simulate malicious attacks. Engagements like this—which sometimes rely on "social engineering" techniques such as leaving an inconspicuous USB stick near a target’s computer—typically seek to identify vulnerabilities, demonstrate their exploitability, and motivate IT administrators and end users to improve their digital security policies and practices.
However, for an "attack" like this to be truly effective (which is to say, truly convincing), it must go unnoticed. If the target—who has probably inserted and removed hundreds of regular flash drives in their life—suddenly hears an unusual sound and sees a pop-up window that mentions a keyboard…there’s a good chance they’ll remove the drive, call the help desk, and embarrass the red team. Avoiding outcomes like that is why I worked so hard to make Diabolic Drive as "stealthy" as possible.
Why Diabolic Drive? And Why Not Use More Powerful Hardware?
While many red-teaming products are capable of sending keystrokes when plugged in, many of them fail to mask their appearance convincingly enough to avoid suspicion. Such devices are often more useful as gimmicky "party tricks" than they are as practical security tools. Other solutions require specific conditions that complicate the social-engineering aspect of a professional engagement. Take, for example, products that masquerade as cables (or as plasma globes). While they are physically inconspicuous (each in its own way), devices like this make me reflect on how long it’s been since I plugged a cable into a USB Type-A port on my computer. (Maybe back in the era of Nokia smartphones running Symbian?) By contrast, I’ve used a flash drive thousands of times!
Diabolic Drive is powered by the ATMEGA32U4 and the ESP8266EX, both of which remain popular today, have excellent community support, and are quite beginner friendly when it comes time to build firmware. And a wide variety of such firmware is readily available, should you need to customize Diabolic Drive to suit your own particular application. Finally, this is a rather specialized tool, and its two primary functions—injecting keystrokes and _not being noticed_—require clever hardware, firmware, and software design but do not require much processing power.
Advantages
- Diabolic Drive exploits the trust associated with commercially available flash-drive enclosures. And, if one enclosure raises suspicion, you can easily swap it out for another.
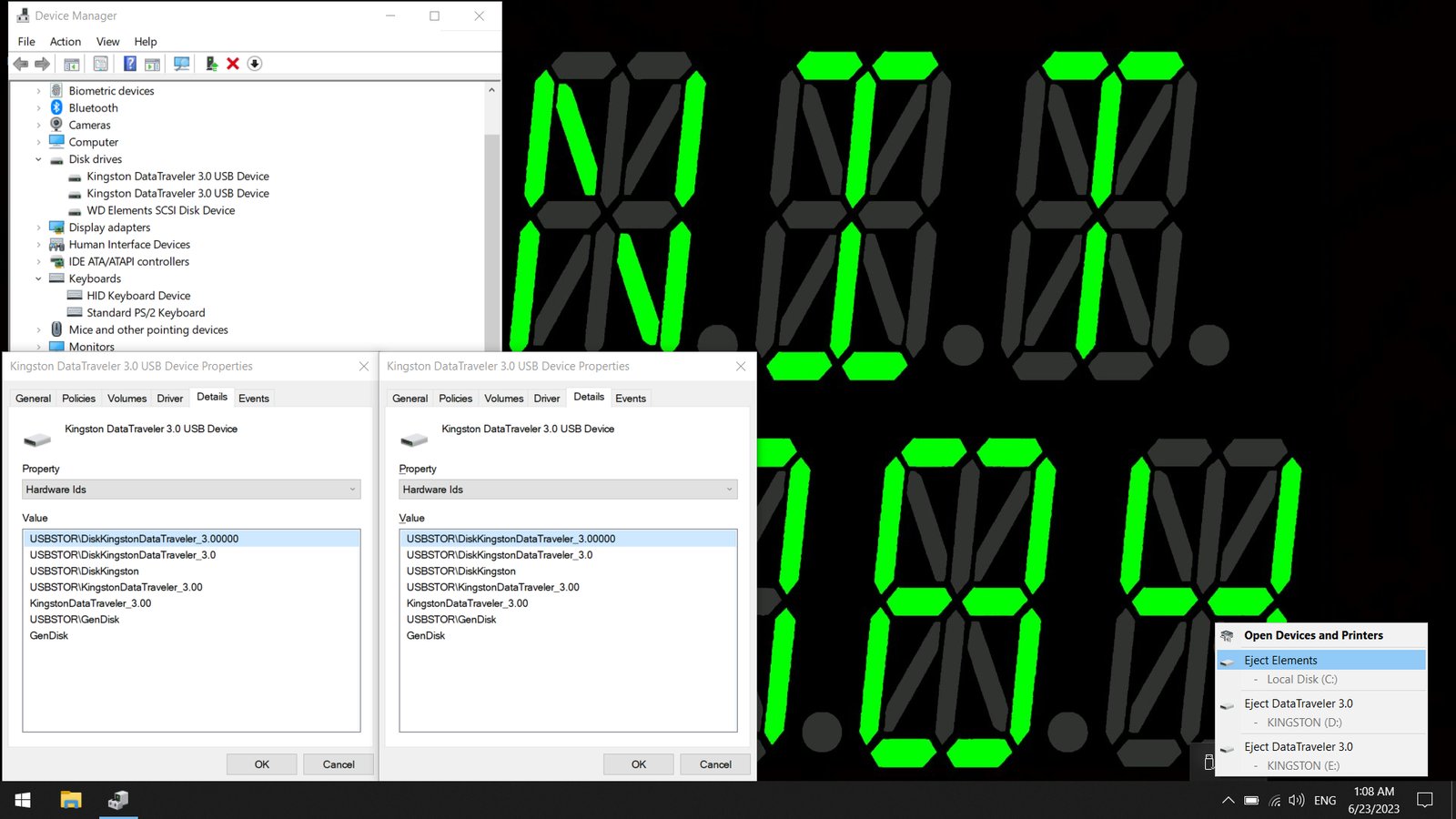
- You can spoof Diabolic Drive's Hardware IDs for maximum stealth, which makes it less likely to generate suspicion, even in the hands of an exceptionally cautious user. (Have a look at the image below. Can you spot which one is Diabolic Drive?)
- When plugged into a host computer, Diabolic Drive functions as a regular USB flash drive with 64 GB of storage. It triggers the usual audio notifications that occur when plugging in a new USB device and offers an average reading speed of 22 MB/s and an average writing speed of 12 MB/s, which is fast enough to ensure stable performance.
- Diabolic Drive has a "Stealthy Mode" that, when active, prevents it from appearing in the Windows Device Manager as a virtual COM port running an Arduino bootloader. Switching to Stealthy Mode requires only a few clicks. You will need access to this virtual COM port in order to program your Diabolic Drive, however, and switching back from Stealthy Mode to Normal Mode requires the use of a separate Arduino device as an in-system programmer. The good news is, Diabolic Drive still works as an HID while it's in Normal mode, so you won't need to switch back and forth when writing, testing, and refining your attack scripts.
Disadvantages
The ESP8266EX module lacks SPI-flash encryption, which might raise concerns about its anti-forensics capabilities in certain engagement scenarios. Keep in mind, however, that you are responsible for obfuscating and encrypting your own code before adding it to a Diabolic Drive "payload." The payload will end up on the target device, and you probably don’t want it exposed if you fail to scrub those logs. Regardless, this has nothing to do with SPI-flash encryption, which would protect the firmware of the keystroke-injection tool itself. Because you will probably be working with open-source firmwares, SPI-flash encryption would have relatively little value for Diabolic Drive. (Though you should take care not to leave clues in any custom firmware you flash if your engagement is such that the Diabolic Drive hardware might be subject to forensic investigation.)
The ATMEGA32U4 supports hardware-ID cloning but it cannot be implemented on the fly. This becomes less of an issue if you identify an HID device connected to your target computer and clone its hardware ID. Doing so eliminates the need to disconnect and reconnect for new IDs to take effect.
Use Cases
Diabolic Drive is a versatile tool for which a skilled red teamer can explore many different applications. We look forward to hearing how you use it!