Project update 14 of 14
Field Report: Flashing a Sonoff Smart Plug with Tigard
by Andrew BI used SecuringHardware’s Tigard and some mini grabbers with male-ended jumper wires to flash Tasmota firmware onto a Sonoff S31 smart plug. It was amazingly easy. Here’s an overview of the process.
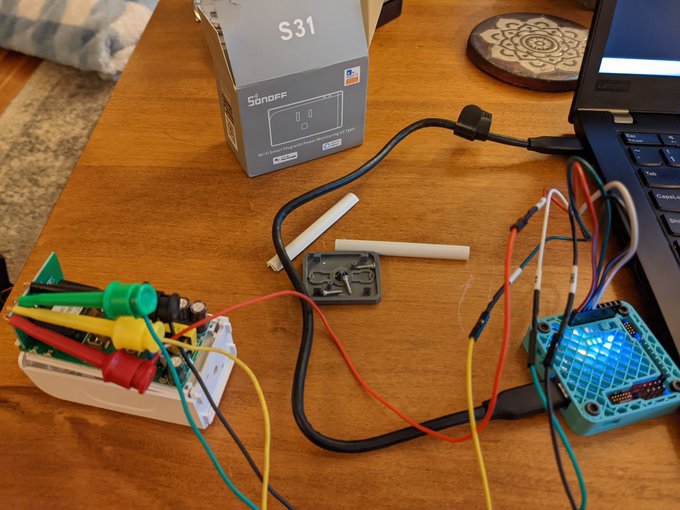
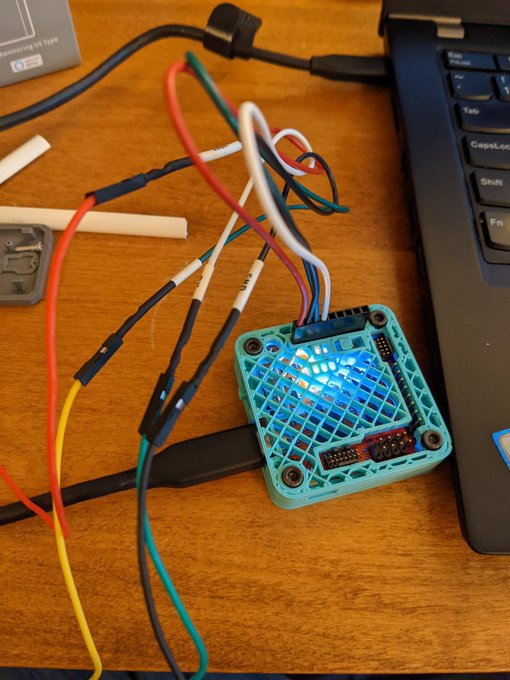
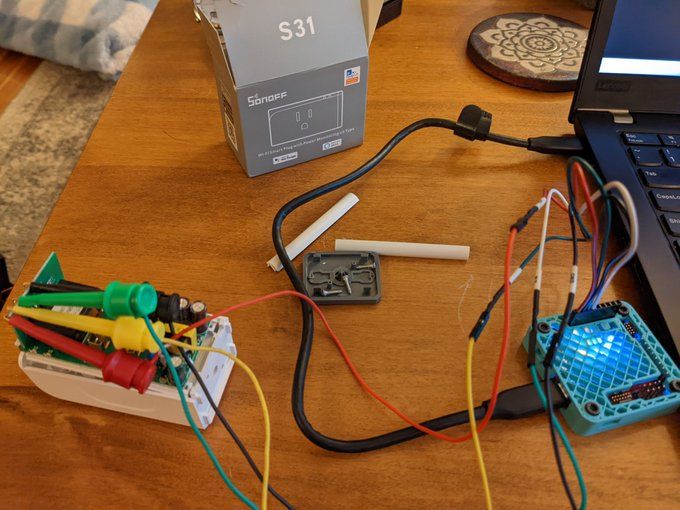
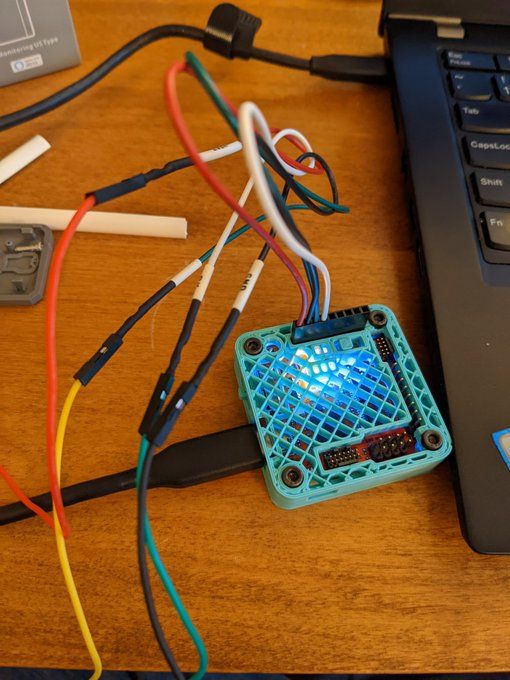
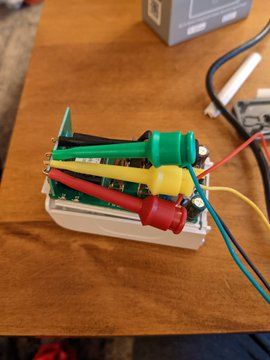
Disassemble the Sonoff S31 and connect mini grabbers to the VCC, RX, TX, and GND test pads on the control board. Connect the UART tail to the Tigard board:
Set the target voltage to 3.3 V and operation mode to UART. Connect the mini grabber jumper wire pins to the UART tail:
- Sonoff VCC to Tigard VTGT
- Sonoff RX to Tigard TX
- Sonoff TX to Tigard RX
- Sonoff GND to Tigard GND
Hold the button on the side of the S31 smart plug and and power up the Tigard and the S31 ESP8266 chip by connecting the USB power supply. Continue holding the S31 button for 10-15 seconds to allow it to enter bootloader mode. Using Chrome, go to https://tasmota.github.io/install to access the web-based installer. Choose your serial COM port and flash the S31 ESP8266 chip.
The Tigard is by no means required for this operation. I have a handful of cheap FT232 boards that could do the trick. But Securing Hardware put so much thought into designing the Tigard that it made the whole process super easy. I love the easy power selection and labeled wires on the tails.
Previously, I’ve used an Adafruit FTDI Friend board to connect to UART devices. That would have worked here as well, but using the Friend board would have required me to cut a trace and solder some pads to re-configure the board for 3.3 V operation. This would take longer than flipping switches on the Tigard and it would have left the board in a semi-permanent 3.3 V configuration. Additionally, I’d have to spend a little more cognitive effort connecting unlabeled jumper wires correctly.
The Tigard allows me to focus my efforts on my project and not on my tools. I really appreciate that. I can see this tool replacing my hodge-podge collection of other USB serial debugging tools.
Note: this report is based on a tweets from this Twitter thread on my account.