Project update 3 of 9
Open True Random Number Generator
The Open-V has the potential to greatly boost and democratize hardware security. As a concrete step toward realizing this potential, we’re happy to announce today that the Open-V will include, at no additional cost, a fully open, state-of-the-art, thermal noise-based true random number generator (TRNG) peripheral. This essential security building block can generate up to 400,000 random bits per second on a power budget of only 240 μW and adds only 0.01 mm2 to the die area, including the necessary advanced peripheral bus (APB) decoder circuitry. Before we describe the TRNG in detail, let’s put it in a larger security context.
Low-level Devices, High-end Risk
The security of the chips you use on a daily basis might be compromised without you knowing it. A camera you use to check on your loved ones, your favorite screencasting device, or even the mic of your smartphone might be prone to leak data. OK, maybe you are an open person and you’re relaxed about your personal data, but imagine what could happen if some of the compromised chips are in health devices or can be used as part of a swarm that might be weaponized to attack critical infrastructure of nations.
A swarm of data-requests to a major DNS provider on October 21st from hacked devices, took down multiple sites including Netflix, Twitter, and GitHub, among other popular sites. Although that particular attack was made possible by a large number of unsecured devices using default passwords, attacks in the future will look for deeper vulnerabilities. The October 21st attack proved you don’t need powerful devices to bring down a large system.
Considering web-enabled sensors are becoming ubiquitous, and most of these sensors are cost sensitive and have limited power, securing every device is becoming more difficult. The market expectation is that consumers won’t pay the price, in terms of both manufacturing cost and expanded power budget, of securing their devices. Even worse, consumers are not aware of the vulnerabilities and risks involved to begin with. For instance, today’s maker community is using undocumented chips to connect and deploy gadgets to the Internet without regard for the trustworthiness of those chips.
Terminology
In her 32C3 talk, Joanna Rutkowska nicely untangled some commonly used (and misused) security jargon . In summary, that jargon is:
- Secure: Resistant to attack.
- Trusted: Something in which you put all your faith, such as a trusted platform module (TPM). If a trusted component of a system is compromised, the entire system is compromised.
- Trustworthy: Deserving of whatever faith you put into it. Trustworthy components behave in predictable ways and conform to a set of specifications.
It’s possible to have secure systems that are not trustworthy (Joanna cites the Intel Management Engine as a possible example), and it’s possible to have trusted systems that are neither secure nor trustworthy.
A Sorry State of Affairs
Currently, it is standard practice for silicon vendors to claim their components are trustworthy because they conform to some standard (e.g., ISO/IEC 11889) and because limited implementation details are available under a heavy non-disclosure agreement (NDA). This notion of trustworthiness is highly inadequate.
Another standard practice in the semiconductor industry is to take a largely reactive position on security - attackers discover vulnerabilities and vendors implement fixes in some future version of their chips, after the damage has already been done. This behavior has led to a culture of hiding specifications in the hope no one finds vulnerabilities. An unfortunate side-effect of this approach is it allows attackers with the best resources to mine vulnerabilities without being detected, thereby dramatically increasing the danger associated with those vulnerabilities. Considering the recent attacks by nation-states, obscuring silicon greatly increases the number of people put at risk. As before, this stance is also highly inadequate.
Despite the large number of chips manufactured every year, the community of people and organizations working on silicon is currently quite frail. For example, even the most powerful nations depend heavily on a small number of offshore chip foundries. This can lead to problems like hardware trojans being inserted at the foundry site. Furthermore, modern SoCs are complex and require a large number of proprietary IP cores, which are becoming harder and harder to trust, especially since they are usually provided as black boxes at the design and verification stages.
Finally, although there is a lot of ongoing research to secure and verify each stage of the supply chain, the associated cost overhead puts such security out of reach of most low-end chips and applications.
Trustworthiness of Open-V
Given the sorry state of affairs just detailed, we believe this open source approach is the best way to build truly trustworthy components deserving of their trusted role in secure systems. By open sourcing the full Open-V specs, along with the schematics and RTL to verify those specs, we hope to ignite security research that will actively detect vulnerabilities and preempt future attacks before they happen. At the same time, open silicon will enlarge the security community, bring more innovation to hardware, and spark a deeper discussion of hardware standards. The more people looking at the security of the lowest layers of computing, the more secure all layers of computing will become.
Open-V True Random Number Generator
A random number generator (RNG) is the most fundamental element of any key cipher or hash function. If a crypto algorithm’s underlying RNG is biased or predictable, the entire crypto algorithm itself is vulnerable to attack from the outset. A true random number generator (TRNG) is a RNG that produces bits based on an underlying random physical process, such as thermal noise. This is in contrast to a pseudo random number generator (PRNG) that generates bits based on a secret key that, if discovered, would allow prediction of all the bits generated.
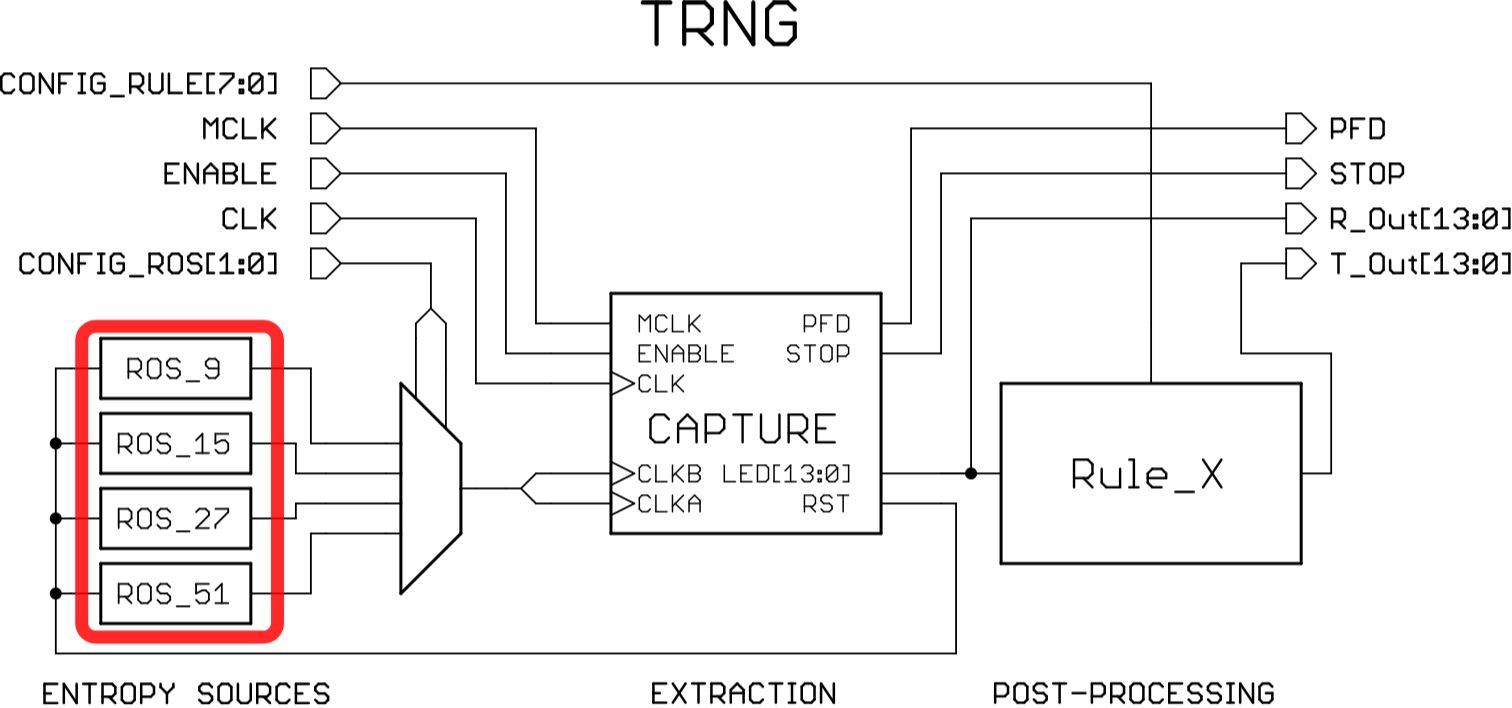
The TRNG we have designed, implemented, tested, and will now include as a peripheral on the Open-V chip is based on a novel combination of a multimode ring oscillator and a cellular automaton (CA). The ring oscillator produces the random bits due to digital edge racing collapsing due to thermal noise. The CA is a postprocessing step used to de-bias the output that requires relatively little die area to implement. The technical details of the TRNG are introduced in a short paper we recently published and will be expanded upon in a longer paper we’ve been invited to submit.
Leaving the implementation details and test results to those papers, the end result is a TRNG with the following properties:
- Process node: TSMC 130 nm GP
- Randomness Verification: NIST Statistical Test Suite
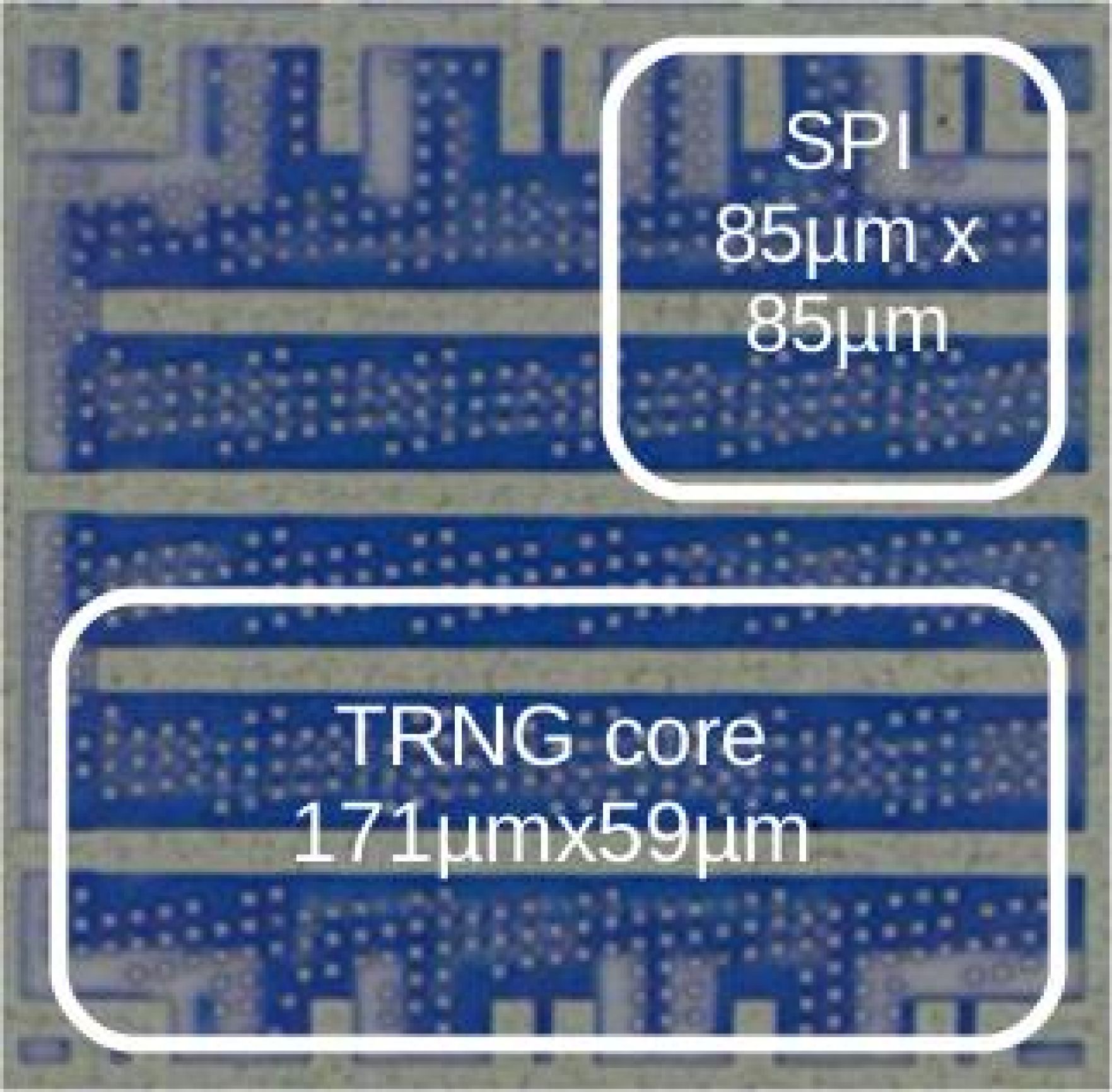
- Die Area: 169 μm x 58 μm (< 0.01 mm2)
- Power Consumption: 240 μW
- Entropy Generation: 400,000 bits/second
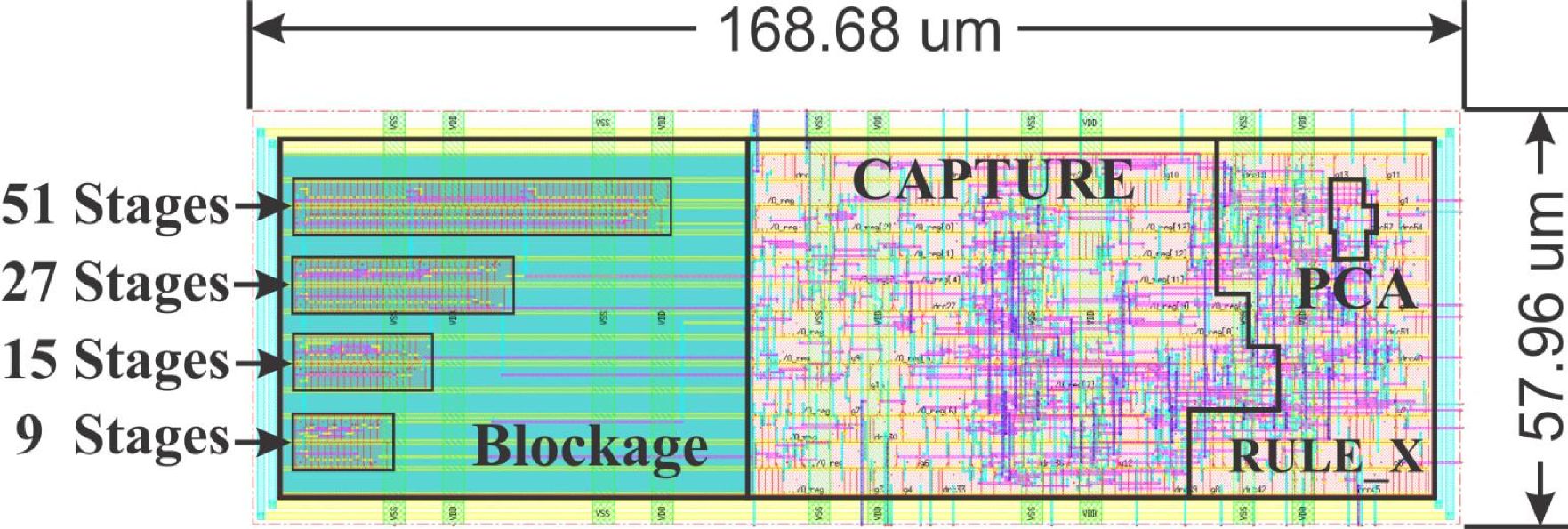
TRNG Implementation Summary
For full implementation details and test results, see the papers listed above. Here, we briefly describe the basic mechanisms of our TRNG and our test results.
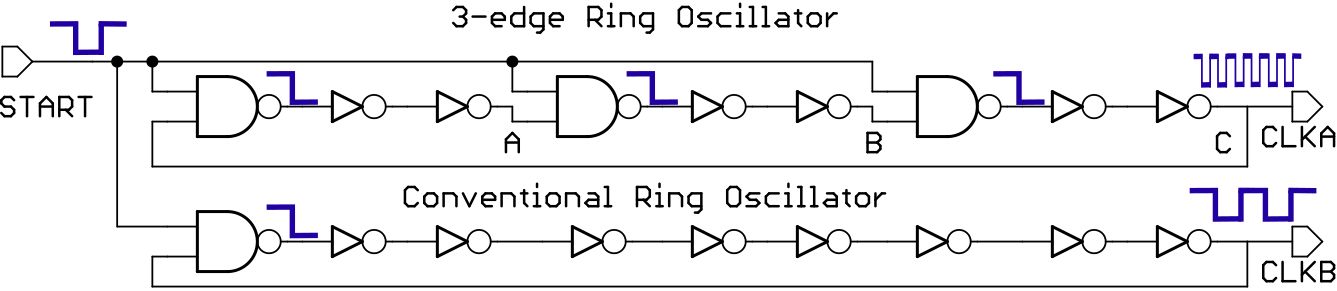
In a conventional ring oscillator, a NAND gate enables and disables the oscillation; when a logical one appears in the enable input START, an edge begins to spread between the inverters until the last stage causing an oscillation with a nominal frequency. In a similar way, when a logical one appears in a multimode ring oscillator, three edges are simultaneously injected into the NAND gates by the signal StART, generating an oscillation at three times the nominal frequency spreading along the ring. As three edges accumulate jitter from thermal noise, eventually two neighboring edges collapse, forcing the ring oscillator to oscillate at the nominal frequency mode.
The extraction of random bits is done through the CAPTURE stage as is shown in the figure below. The method to extract random bits consists of counting the cycles of the three-edge ring oscillator until a collapse occurs with a 14-bit cycle counter. A digital phase frequency detector (PFD) identifies the frequency collapse event and triggers the output register.
Because the captured results from the entropy source still have some biasing, a postprocessing stage is needed to improve entropy results. In our TRNG, postprocessing is performed by a cellular automaton. The exact rule used in the CA was determined by exhaustively testing all possible rules on a data set of 1.4 Mbits captured from the multimode ring oscillator entropy source. Our results (see table below) show that six of the rules outperform doing no postprocessing (Non Rule). See the NIST Statistical Test Suite for details on each of the tests and our short paper for more details in general.
Measured NIST Randomness Test Results Over 100 Tests
| NIST Test | Non Rule | Rule 51 | Rule 75 | Rule 85 | Rule 105 | Rule 150 | Rule 180 |
|---|---|---|---|---|---|---|---|
| Frequency | 94 | 94 | 98 | 97 | 100 | 100 | 98 |
| BlockFrequency | 95 | 95 | 100 | 100 | 99 | 99 | 100 |
| CumulativeSums | 93 | 93 | 99 | 97 | 100 | 100 | 99 |
| Runs | 98 | 98 | 90 | 96 | 99 | 99 | 90 |
| LongestRun | 99 | 98 | 100 | 98 | 99 | 100 | 100 |
| Rank | 99 | 99 | 99 | 97 | 97 | 99 | 98 |
| FFT | 99 | 99 | 100 | 99 | 100 | 100 | 100 |
| NonOverlappingTemplate | 146 | 146 | 142 | 146 | 148 | 148 | 142 |
| OverlapptingTemplate | 100 | 99 | 98 | 100 | 98 | 99 | 98 |
| Serial | 98 | 98 | 97 | 97 | 99 | 99 | 97 |
| LinearComplexity | 96 | 99 | 100 | 98 | 97 | 99 | 99 |
| ApproximateEntropy | 91 | 91 | 98 | 97 | 90 | 90 | 98 |
| Sum | 1208 | 1209 | 1221 | 1222 | 1226 | 1232 | 1219 |
Conclusion
One of the main benefits of open silicon is that it is trustworthy as the basis for secure computing. Not only is Open-V the world’s first fully open microcontroller (CPU and peripherals), but with the addition of an open TRNG peripheral (also a first, as far as we know), Open-V becomes a real platform for concrete security applications in the real world. Although the TRNG is just one component of the hardware root of trust, it is an essential element of a more complex secured environment. We look forward to seeing what you will do with it!