As ChipWhisperer-Husky gets close to entering the end of the campaign, we wanted to share some of the new features you’ll get to enjoy. Our final update during the campaign next week will include a sneak peek at how we test units as we prepare for production. But in the meantime, we wanted to recap what makes the ChipWhisperer-Husky so much more exciting than the previous ChipWhisperer-Lite:
- Doubles the maximum sampling frequency
- External PLL allows sampling at many multiples of the target frequency (not limited to x1 or x4)
- 2 more bits of ADC resolution
- Streaming for unlimited captures
- 4x more storage
- More triggering options
- Better glitch control and more glitch options
One totally new feature is something we call TraceWhisperer. Ok but what *is TraceWhisperer, you ask? It’s a sniffer for Arm debug trace data. Arm trace is incredibly powerful and flexible in its ability to tell you what an Arm processor is doing and when. In Husky, this information can be used to trigger a capture or glitch attack, or simply annotate a capture with additional information about what the target was doing as a function of time.
This is different from just setting breakpoints since the instruction trace doesn’t require you to pause the program. For power analysis or fault injection, this would mean you can set trigger points based on specific functions, and a whole lot more.
Husky brings to life the third incarnation of TraceWhisperer, and we’re excited to see what our users will do with it now that it’s a more easily accessible as a standard Husky feature. TraceWhisperer started life in DesignStartTrace. We saw its potential right away, but DesignStartTrace is limited to users with a CW305 FPGA target board and an interest in running Arm Cortex processors on an FPGA. In its second incarnation, TraceWhisperer was ported to the PhyWhisperer-USB platform as an alternative FPGA bitfile. Now with Husky, we’re finally putting the power of trace in the hands of every Husky user, in a single device that can capture power traces and Arm-debug traces simultaneously.
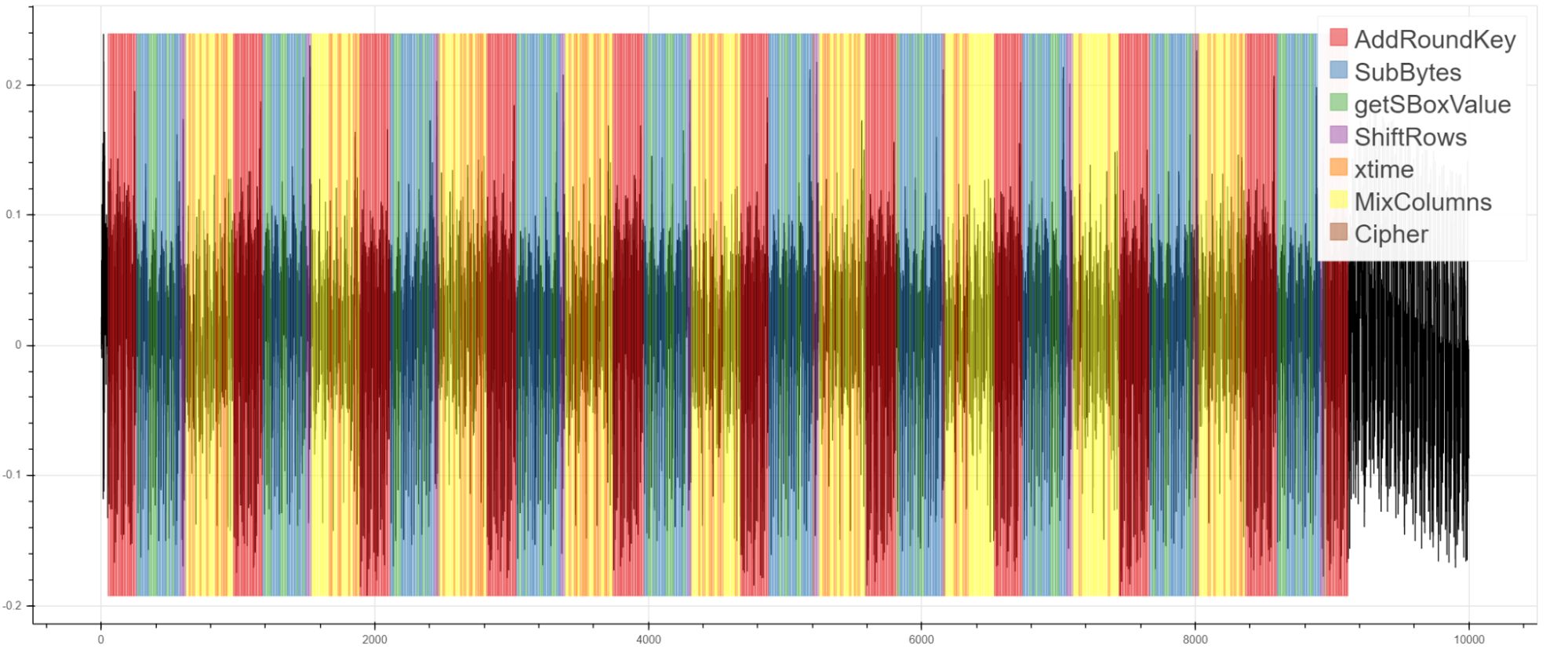
Have a look at the DesignStartTrace page for some basic examples of how trace can be used in the context of side-channel work, like this neat visualization of AES:
We already have a couple of notebooks to teach you the basics of using trace, and this notebook shows how trace can be used to facilitate building an attack on micro-ecc.