Project update 2 of 8
CANtact Pro & SocketCAN
by Eric EHi, and thanks for checking out CANtact Pro!
In the first update, we’re going to be looking at how to use the CANtact Pro on Linux with SocketCAN. This provides access to a wide range of open-source tools. We’ll get to Windows and macOS support in future updates.
Configuring CANtact Pro
Out of the box, CANtact Pro will appear as a SocketCAN device on Linux. Plug it in, and you’ll be greeted with two devices.
$ ip link show | grep can
20: can0: <NOARP,ECHO> mtu 16 qdisc noop state DOWN mode DEFAULT group default qlen 10
link/can
21: can1: <NOARP,ECHO> mtu 16 qdisc noop state DOWN mode DEFAULT group default qlen 10
link/can
Now that our devices are available, we’ll need to set them up. The most important setting is bitrate. The bitrate of all devices on a CAN network need to match. Commonly used bitrates are 1000000, 500000, 250000, and 125000, though others exist. These values are given in bits per second. We set the bitrate up with the ip command:
sudo ip link set dev can0 type can bitrate 500000
This command sets the bitrate of the can0 device to 500000 bits/s. With that done, we’re ready to enable the device:
sudo ip link set can0 up
This enables the can0 channel of the device. The corresponding LEDs on the device will light up once the channel is enabled.
Now we’re ready to use our device! There’s a wide variety of software that supports SocketCAN, and therefore CANtact Pro.
Basic CAN Utilities
Lets start with the can-utils commands. These will need to be installed on your system. On Debian and Ubuntu, they can be installed with apt:
sudo apt install can-utils
Now we can send and receive frames! We will use cangen to generate some traffic on can0:
cangen can0
In another terminal, we use candump, to display every received frame.
$ candump can0
can0 076 [4] 09 1D 36 34
can0 511 [0]
can0 2A7 [8] 1A E1 DC 6B 36 D8 10 38
can0 4A9 [1] 0E
can0 170 [1] B5
can0 0C7 [8] 69 12 0E 62 90 3D 6A 2F
can0 50B [8] A8 14 8B 4D BD 2B D2 6C
can0 32E [3] 32 79 03
can0 428 [8] E8 66 BE 58 39 51 F5 08
can0 3AC [8] D0 03 26 31 53 3E 47 3D
can0 767 [8] 8A 16 58 75 10 1C E7 1B
can0 00B [8] 15 6E 5B 39 7B F9 EA 3A
can0 3C9 [8] 54 F3 D1 05 90 0C D1 09
...
We use cansend to send single frames. The format of the command argument is [ID]#[D0][D1][D2][D3][D4][D5][D6][D7] where D0 - D7 are data bytes. All values are given in hexadecimal. For example, to send a frame with ID 0x123 and data AA BB CC:
cansend can0 123#AABBCC
cansniffer
The cansniffer utility is very helpful for reverse engineering CAN networks. It shows CAN data and highlights which bytes are changing. A common technique for reverse engineering CAN networks is to watch which bytes change when an action is taken. For example, watching cansniffer‘s output while manipulating the throttle will make it easy to see which bytes correspond to throttle position.
Wireshark
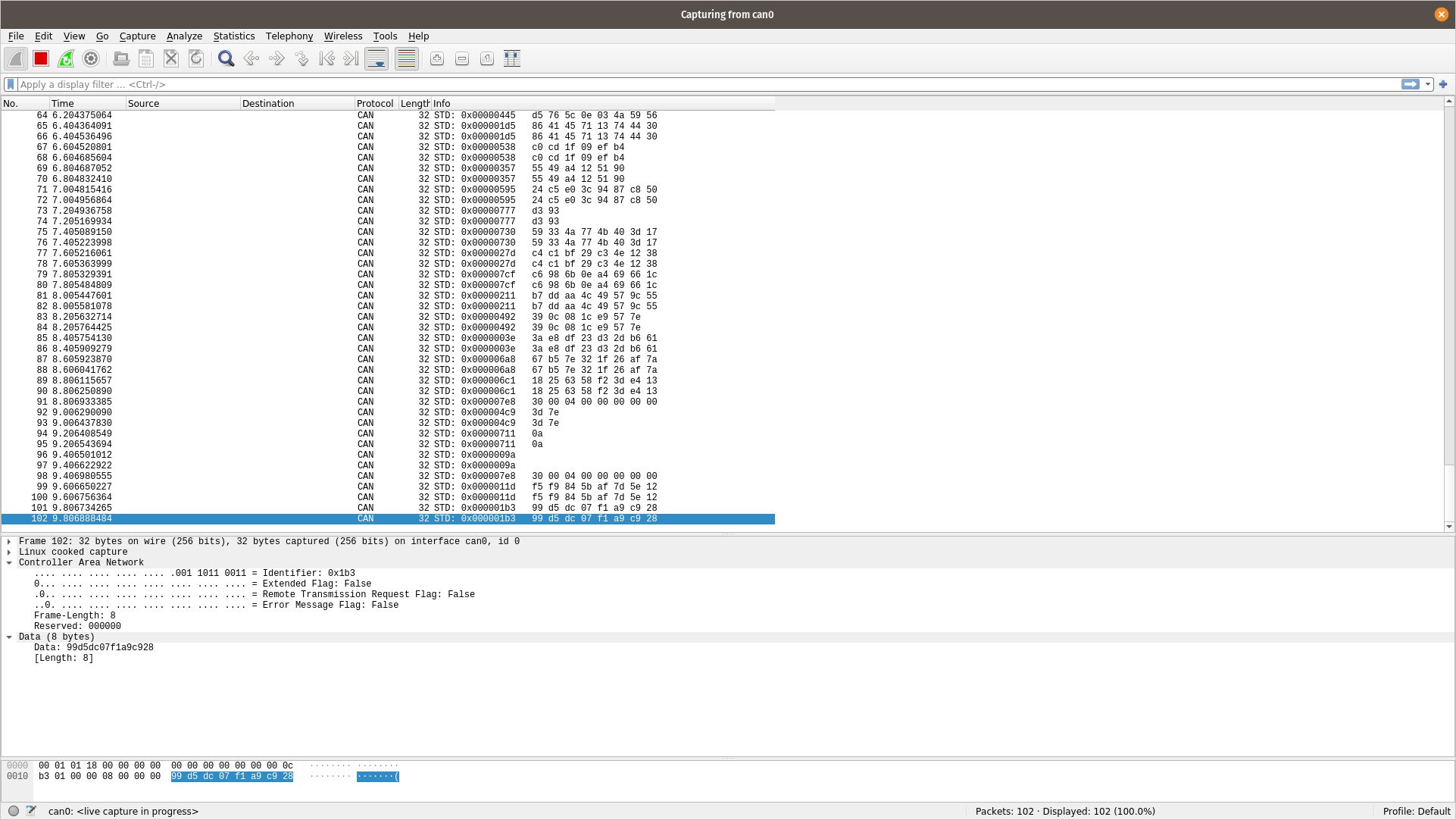
Wireshark is a popular tool for analyzing network traffic, and it contains support for CAN. To start capturing traffic, open Wireshark and select a SocketCAN interface.
The Wireshark trace window will start displaying CAN traffic. To demonstrate, we’ll generate random frames using cangen.
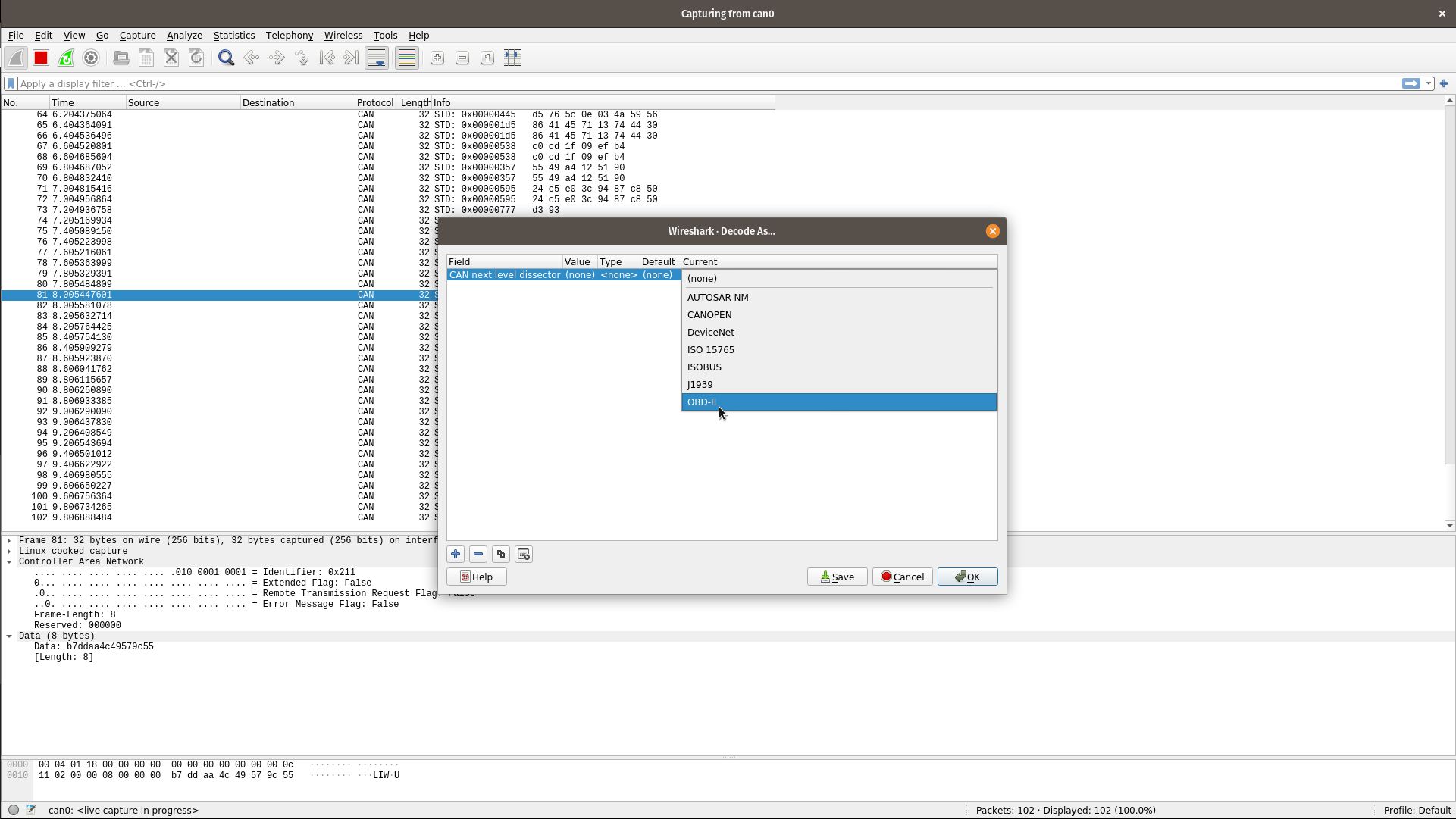
Wireshark also contains decoders for some common CAN protocols. To access these, right click on any CAN frame, then select "Decode As…". The decoder is selected under the "Current" column.
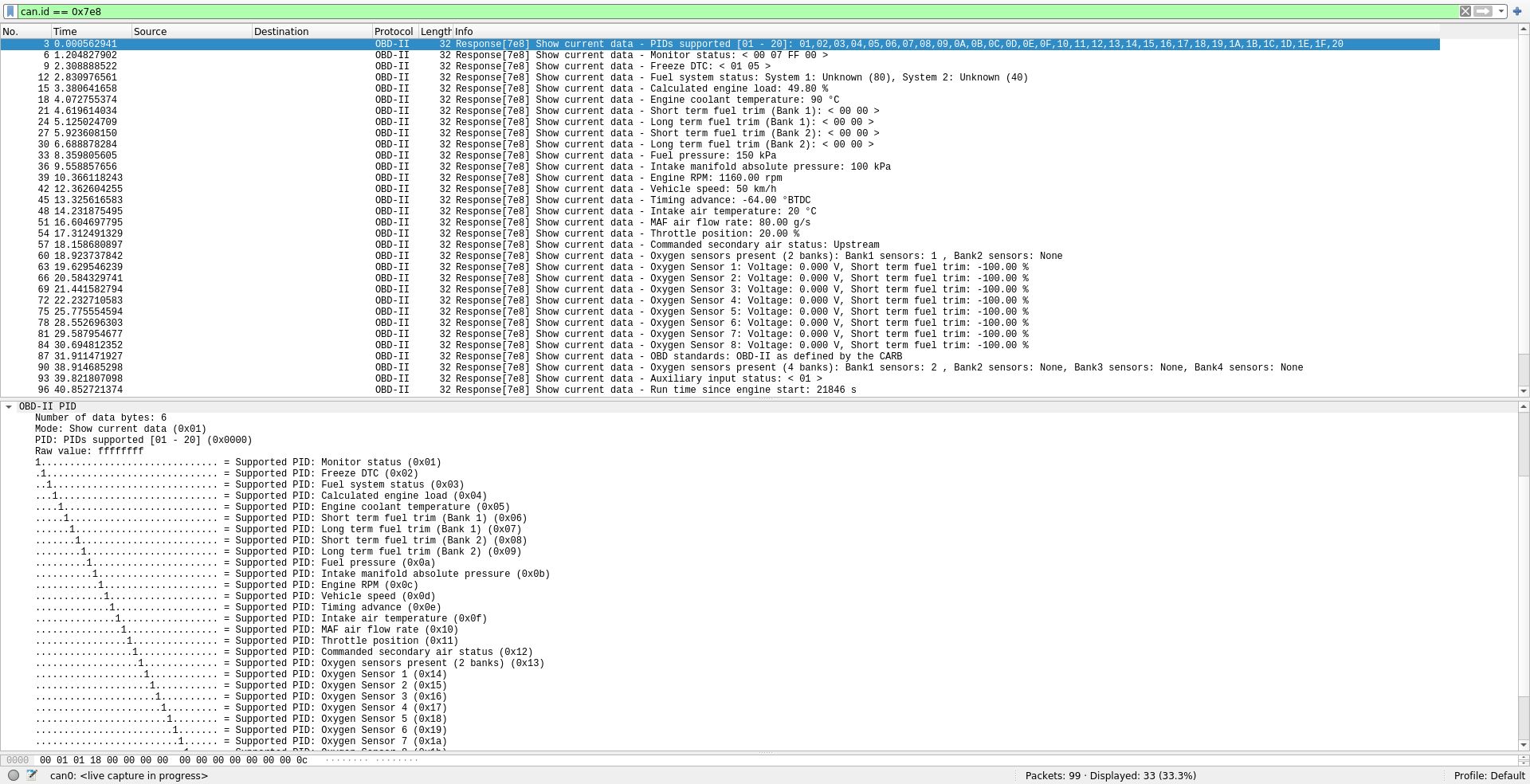
Now we’ll decode some OBD-II PIDs. We use cansend to request an OBD-II PID, then view the result in Wireshark. Here, we’re requesting PIDs 00 to 20 using OBD-II Mode 1. Wireshark will decode the PIDs into real world values for us.
Identifying a Channel
Have you ever had multiple CAN interfaces connected and been unsure which is which? CANtact Pro supports an "identify" feature that lets you find a channel easily. This can be enabled using ethtool:
sudo ethtool --identify can0
This will blink the LEDs for the can0 interface, making it easy to find.
Other Tools
There’s a ton of SocketCAN tools out there. Some other notable tools include: