Identity: The Killer App of Crowdfunded Open Hardware

In the next 20 years, the notion of a secure, verifiable identity will be the killer app that drives the adoption of crowdfunded open hardware.
Good ideas, they say, are a dime a dozen. The real skill lies in their execution. Entrepreneurship is the process of managing the risk involved in turning an idea into a product.
Traditionally, there have been two dominant ways of managing this risk: taking it all on oneself by bootstrapping, or offloading it to large investors, like banks and venture capital firms, in exchange for equity. However, over the last decade, crowdfunding has emerged as an alternative to these traditional forms of risk management. In fact, it’s estimated that more money is now raised in the United States through crowdfunding than venture capital¹. Seldom understood, though, is that crowdfunding is not just an alternative funding strategy, but a funding strategy that allows the pursuit of entirely new classes of ideas previously inaccessible to entrepreneurs. Of particular interest is the class of ideas loosely described as open hardware.
Open Hardware
Roughly speaking, open hardware is the physical analog of open source software. Just as the source code of open source software is freely available for viewing and modification, the design files – the schematics, layout, mechanical CAD, firmware, bill of materials - that go into making a physically open hardware product can be inspected and altered, subject to the exact licenses used. The difference between open hardware and open source software is simply one of cost: manufacturing hardware is orders of magnitude more expensive, both in terms of time and money, than developing equally complex software. Bits are cheap, atoms are expensive.
Because nearly all companies, whether they know it or not, rely on and use open source software in one way or another, there is a healthy market for enterprise service providers of open source software. Companies such as Redhat, Puppet, and Docker that build and maintain open source software, and make money from enterprise sales of premium versions.
However, the same is not true of open hardware: hardly anyone owns, let alone uses, open hardware, and so, there is no market for enterprise-level service providers. Creating such a market would require a massive amount of capital investment in manufacturing and distribution. Since banks don’t invest in unproven strategies, and venture capital firms don’t invest in ideas that can be easily copied, traditional funding strategies for open hardware are out. That leaves crowdfunding.
In fact, crowdfunding is particularly well-suited to the demands of open hardware development and deployment. Both crowdfunding and open hardware rely on collective action at the grassroots level, so people drawn to one are likely be more receptive to the other. Moreover, the resulting market of crowdfunded open hardware is, in theory, quite efficient. Consumers can directly influence, or even become, producers without the mediation and undue influence of third-party investors whose incentives may often be very different. Simply stated, crowdfunding is necessary for the widespread adoption of open hardware.
Why is there a market for open hardware? Who wants to buy it, and why? We’ve thought a lot about these questions over the years at Crowd Supply – a company I co-founded as a place dedicated to bringing original, useful, and respectful hardware to life. Customers of open hardware are a diverse group - multi-national corporations, nation-states, school children, hopeful parents, hardened engineers, and self-proclaimed crypto-anarchists. Their reasons for wanting open hardware also run the gamut, but can be boiled down to one or more of the rights listed in Crowd Supply’s Proclamation of User Rights. The Proclamation defines a set of users’ rights and their implication for creators of open hardware, and is quite similar in nature to open source software licenses. At its core, it is a statement of support for the curiosity, independence, privacy, and security of the user.
An Economic Case for Open Hardware
In working with product designers and engineers to bring their ideas to market, we have seen firsthand how creators benefit economically from opening their products.
Early adopters understand the value of being able to explore and modify a product, and to make it do things beyond the creator’s original intent. In fact, open products can outlast their creators and grow as the community sees fit. The Novena Open Laptop provides an example. Although aimed at a niche market of engineers, the product raised over $750,000 through crowdfunding and was used as the basis for several other projects, including the CrypTech hardware security module. The community appreciates the fact that open products are inherently more secure and not tethered to their manufacturers. These early adopters are worth much more than the money they pay for the product. They will be the product’s most ardent evangelists, especially if the philosophy behind the product is one they already support. For example, the LimeSDR project was able to raise over one million USD due to good word of mouth among its backers.
Moreover, opening a product can lead to faster development cycles since the communities built around open hardware products often consist of people interested in helping with the product development itself, not just using the end- product. An example is the Ultimate Hacking Keyboard, which raised over $500,000, and has benefitted from extensive firmware development by several community members.
Finally, open hardware involves less logistical overhead. Protecting and hiding intellectual property can be time consuming and expensive. In addition, many services, like GitHub, don’t require payment if the final product is open in some way. The EEZ H24005 Benchtop Power Supply is a good example of a project enjoying these benefits. The project’s backers, who contributed over $120,000 to bring it to life, can follow development progress via the project’s hardware and software repositories.
Crowdfunded Open Hardware’s Killer App
For any existing product, there could, in theory, be a crowdfunded open hardware version. The EEZ H24005 Benchtop Power Supply and the Ultimate Hacking Keyboard previously mentioned are good examples. It’s not just that crowdfunded open hardware versions of these products are possible - there are strong arguments that they are superior, precisely because they better honor the user rights outlined above.
In addition to existing products, crowdfunded open hardware enables entirely new categories of products. At present, the most prominent such category deals with computing privacy and security – products that protect computer users, their data, and their communications from tampering or theft by hardware manufacturers, network service providers, governments, social media companies, and any of the other myriad potential adversaries the average computer user encounters every single day.
The problem of computing privacy and security is a large, and multi-faceted one, the solution to which is equally complex and involves everything from social behavior to network protocols. At the very core of the solution is the quest for a decentralized, verifiable, and persistent identity for each user. Some not-too-distant application of strong cryptography - perhaps in the form of a blockchain technology - will likely bring about exactly such an identity mechanism. However, there is a critical missing piece in making this a reality: the hardware on which this strong cryptography is to be executed.
The killer application for crowdfunded open hardware is exactly the device that stores and manipulates the root of trust serving as the foundation of a decentralized, verifiable, persistent identity. Think of it as the "totem" used to distinguish reality from dreams in the 2010 movie Inception.
Towards Trustworthy Hardware
The journey toward an "identity totem" has followed a meandering path and is far from over, though there has been significant progress and the next steps are becoming ever more clear. What follows is a broad selection of products launched on Crowd Supply that qualify in one way or another as crowdfunded open hardware and mark some waypoint on this journey. Each illustrates a different set of choices between pricing and performance, open versus proprietary, and meeting users where they stand as opposed to pulling them to the destination.
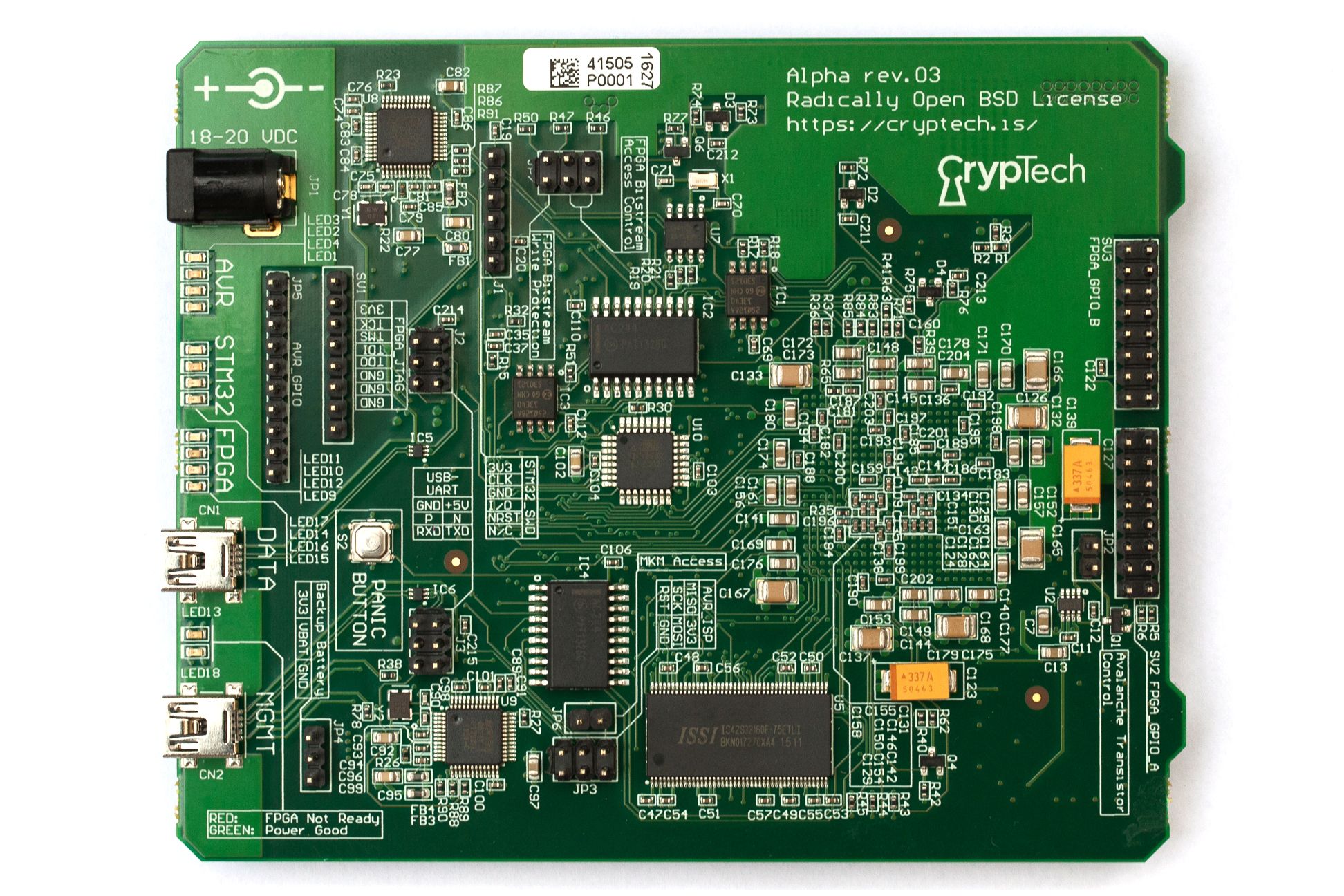
CrypTech Alpha
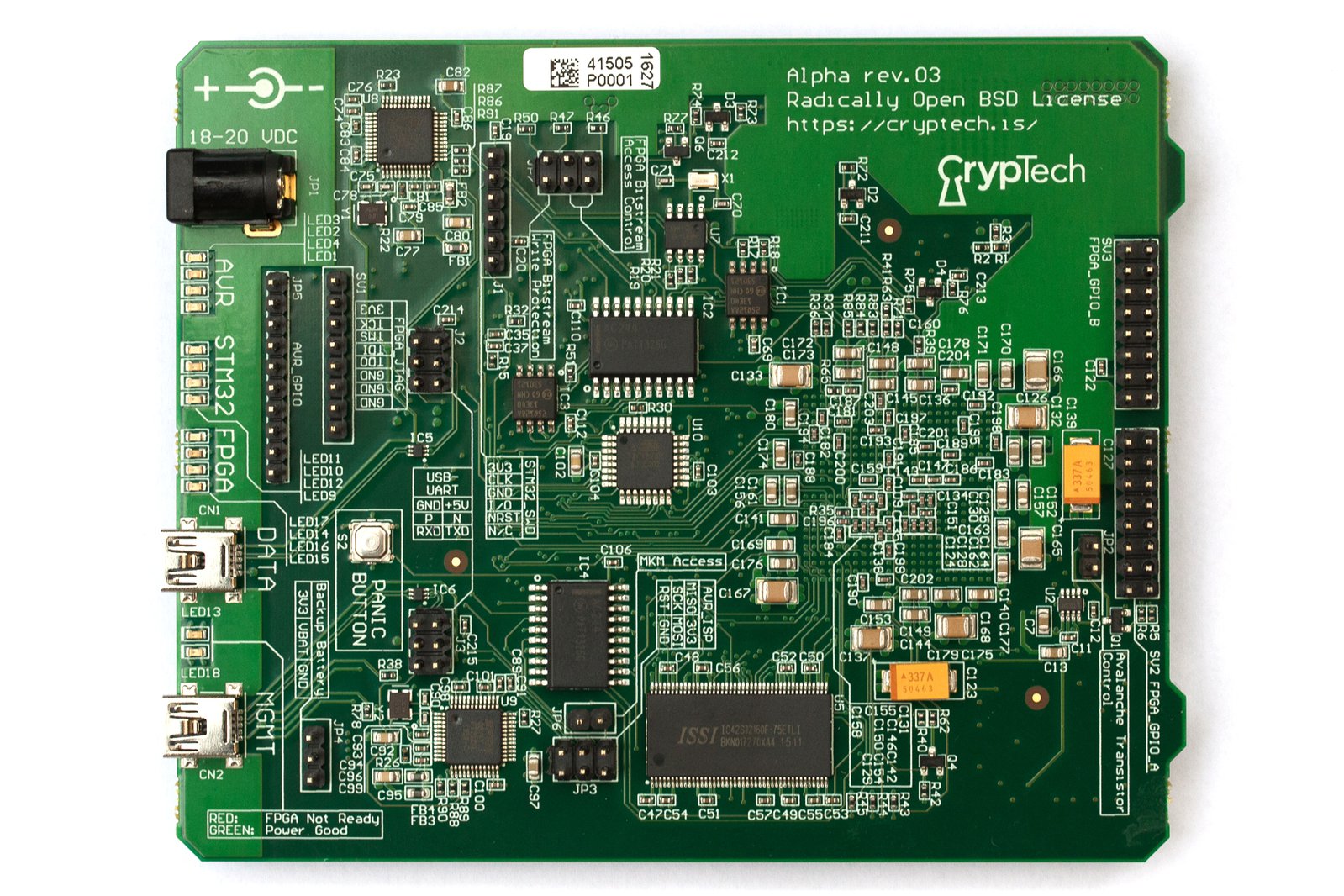
The prototype of an inexpensive, open source, cryptographic engine developed independently by an international team, CrypTech Alpha is a hardware security module (HSM), a specialized device used to securely store the public/private key pairs used with digital certificates. This is the kind of device a bank would use to secure its data and transactions. Almost without exception, the backers of the CrypTech campaign were the developers of the project themselves, raising nearly five times the $4,000 funding goal.
While the CrypTech team certainly did use crowdfunding as a way to cover some basic development costs, their primary interest seems to have been in using Crowd Supply’s fulfillment service to simplify the logistics associated with a decentralized, international team of developers. The important lesson here is that there is much more to creating a product than simply raising the money to manufacture it.
Pastilda
A small, open source, hardware password manager that acts as a middleman between your computer and your USB keyboard. During normal operation, Pastilda passes keystrokes from the keyboard directly to the host computer, as if it weren’t there at all. However, when a special key combination is entered, it enters a special mode that allows you to manage and make use of any of the encrypted passwords stored on it.
Pastilda raised over $9,000 from security-conscious computer users, some of whom already used the KeePass software but were looking for more security at the hardware level. You don’t have to be a bank to care about digital security. The example of Pastilda demonstrates how more and more people are looking for better options to keep their data secure, and realizing the inherent benefits of open hardware when it comes to security and control.
ORWL
A physically secure personal computer that will instantly erase all data as soon as it detects tampering with its secure enclosure. The underlying technology is the same as that used in secure payment terminals. The idea is to treat all data with the same level of security traditionally reserved for financial data. The ORWL campaign raised over $100,000 from a wide range of backers - from information security professionals to casual computer users concerned about the security of their data. ORWL has, however, also been the target of some criticism. You see, at the heart of ORWL’s security lies a secure microcontroller with specialized features for detecting tampering and carrying out cryptographic operations that secure the entire computer.
Now while this is a very sophisticated technology, it is also one that is quite proprietary - even getting the datasheet requires a non-disclosure agreement with the manufacturer of the chip. This fact has not gone unnoticed amongst users, who argue that the entire system is only as secure as its root of trust. In this case, there is no way to verify whether the root of trust is indeed secure and contains no backdoors.
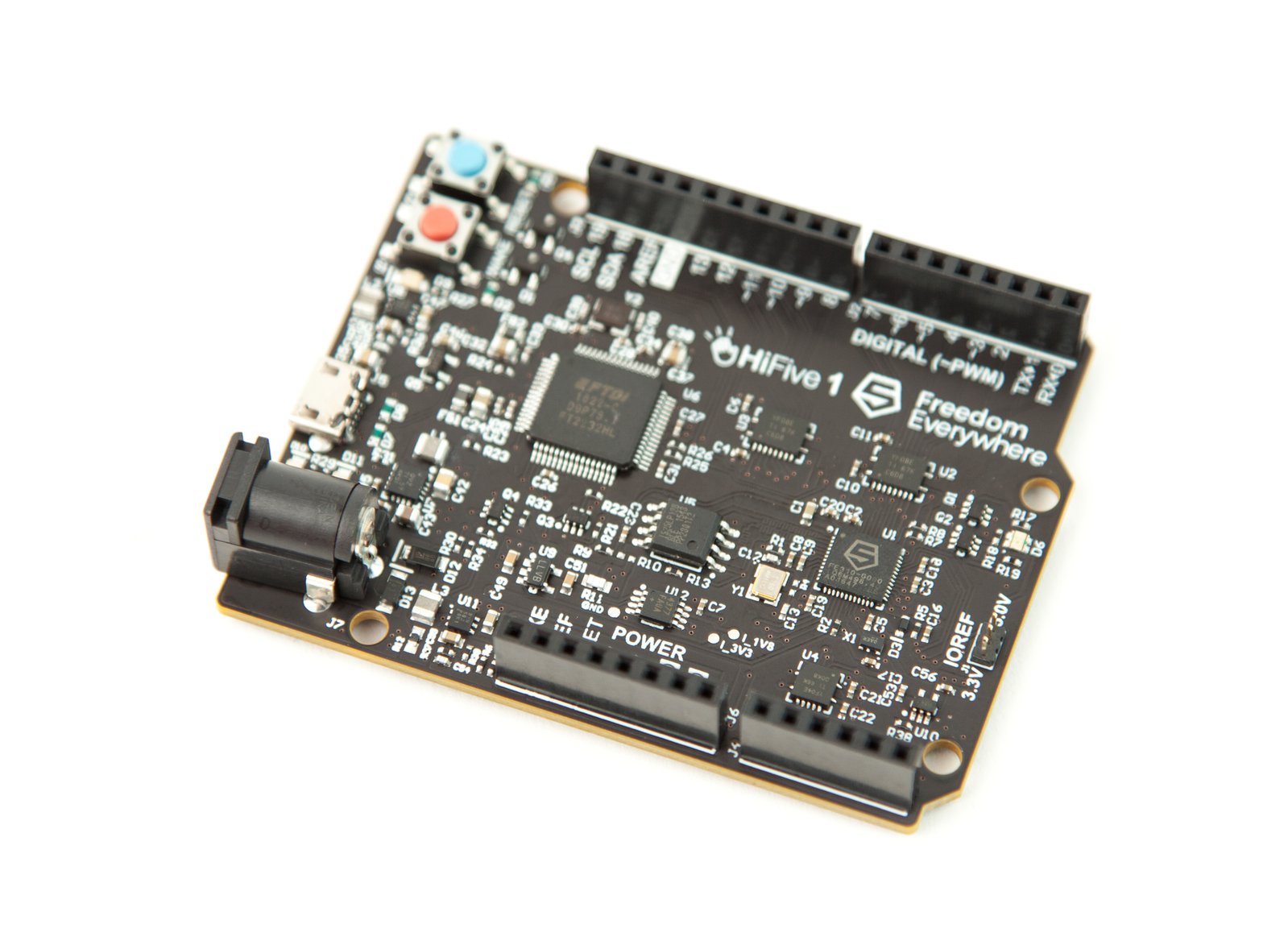
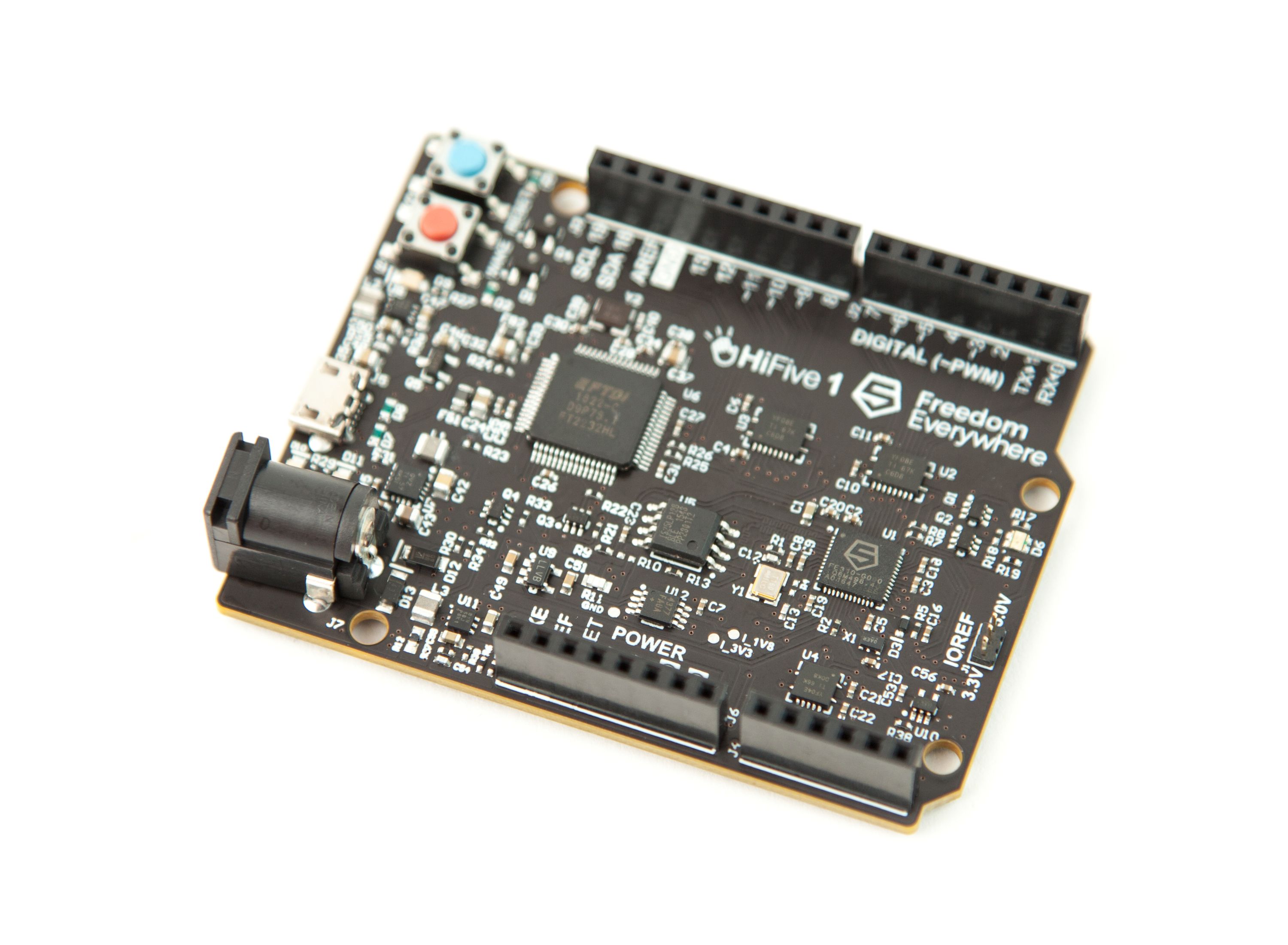
HiFive1 Development Board
An Arduino-compatible development board for a 32-bit microprocessor with a CPU based on the open source RISC-V instruction set architecture (ISA), the HiFive1 is the very first commercially available RISC-V silicon. The project raised over $70,000 from a diverse group of RISC-V enthusiasts, Arduino makers, embedded systems researchers, robotics startups, and supporters of open silicon.
Until the HiFive1 project, the RISC-V ISA had largely been relegated to research labs and simulation. Releasing an actual product based on RISC-V set a clear precedent for others to follow, and serves as a warning to the entrenched x86 and ARM architectures that the market is seeking more openness. The potency of this threat at present, however, is minimal given that the microprocessor chips themselves are not yet available other than as a component on the HiFive1 board.
Open-V Microcontroller
The Open-V project aims to bring into mass production a RISC-V-based microcontroller that is open source all the way down to the transistor level. Like the HiFive1, the Open-V project offers an Arduino-compatible development board. Unlike the HiFive1, however, the entire microcontroller - not just the CPU - is open source, and the Open-V chips will be mass produced and available for incorporation into other products. The Open-V’s rich set of peripherals include a true random number generator, analog-to-digital and digital-to-analog converters, timers, and several serial communication interfaces. At the time of writing, the Open-V crowdfunding campaign [https://www.crowdsupply.com/onchip/open-v] is still running and has gained the support of several hundred people, but is still far from the ambitious $400,000 funding goal needed to take a silicon design into mass production. It serves as an example of how bringing a completely custom semiconductor design to mass production is a long, expensive undertaking. It remains to be seen if the considerable support across a wide array of communities will be sufficient to make the Open-V a reality.
The Open Hardware Trilemma
The aforementioned examples all hint at a fundamental trilemma - when it comes to open hardware, as with car mechanics, you only get to choose two from: good, fast, and cheap. Three projects in particular illustrate this trilemma.
First, there is the Librem line of laptops, which raised over one million USD based on the promise of protecting user freedoms. The concept was simple: build modern, high-performance, affordable laptops using only hardware that doesn’t require proprietary software to run. The concession they made was to use Intel chipsets, which are widely reported ² to be a threat to user security. So, while the Librem laptops are fast and cheap, they aren’t as good (i.e., open) as many would like.
In contrast, the EOMA68 project raised over $200,000 to offer an undeniably good and cheap computing alternative in its $65 computer cards that run only libre firmware and software. Where the EOMA68 projects falls short is speed - its ARM processor puts it solidly in the category some deride as "retrocomputing," even if faster versions are already in the works.
To round out the trilemma illustration, there is the Talos Secure Workstation, which raised over $500,000, but failed to meet its $3.7 million funding goal. Had the campaign succeeded and Talos been produced, it would have been among the highest performance computer workstations on the market, sporting up to 256 GB of DDR3 ECC RAM, 96 logical cores, and a clock speed of 3.857 GHz. What truly set it apart, though, were its extremely high standards of openness and auditability. Of course, all that came at a price - a fully built workstation started at $17,600, placing it well out of the "cheap" category.
The good/fast/cheap trilemma will become less of a problem for open hardware as users gradually come to appreciate the value of privacy and security. Alternatively, the prospect of bypassing the trilemma altogether is beginning to materialize in the form of open silicon.
Trust, Security, and Open Silicon
Several information security specialists have pointed out the difference between ‘trusted’ and ‘trustworthy’ - the former entails blind faith, whereas the latter entails earned trust. Open silicon, which is the ultimate expression of crowdfunded open hardware, is the only path to trustworthy hardware. The first open silicon chips won’t compete with the processors used in modern laptops, but they may be sufficient for more modest, but equally important devices, such as a decentralized, verifiable, persistent identity totem. The HiFive1 and Open-V projects are significant proof points, and others will soon follow. The path to a completely trustworthy computing platform will, of course, be a long one. Each milestone along the way must be simultaneously good, fast, and cheap enough to gain widespread adoption. Nonetheless, the first steps have been taken and it’s sure to be an interesting journey.
References:
This post was originally published in the Startups and Entrepreneurship issue of XRDS: Crossroads, The ACM Magazine for Students, Volume 23 Issue 4, Summer 2017. Download a free PDF of the original article.
¹Barnett, C. Trends Show Crowdfunding To Surpass VC In 2016. Forbes. June 9, 2015.
²Eckersley, P. and Portnoy, E. Intel’s Management Engine is a security hazard, and users need a way to disable it. Electronic Frontier Foundation. May 8, 2017.